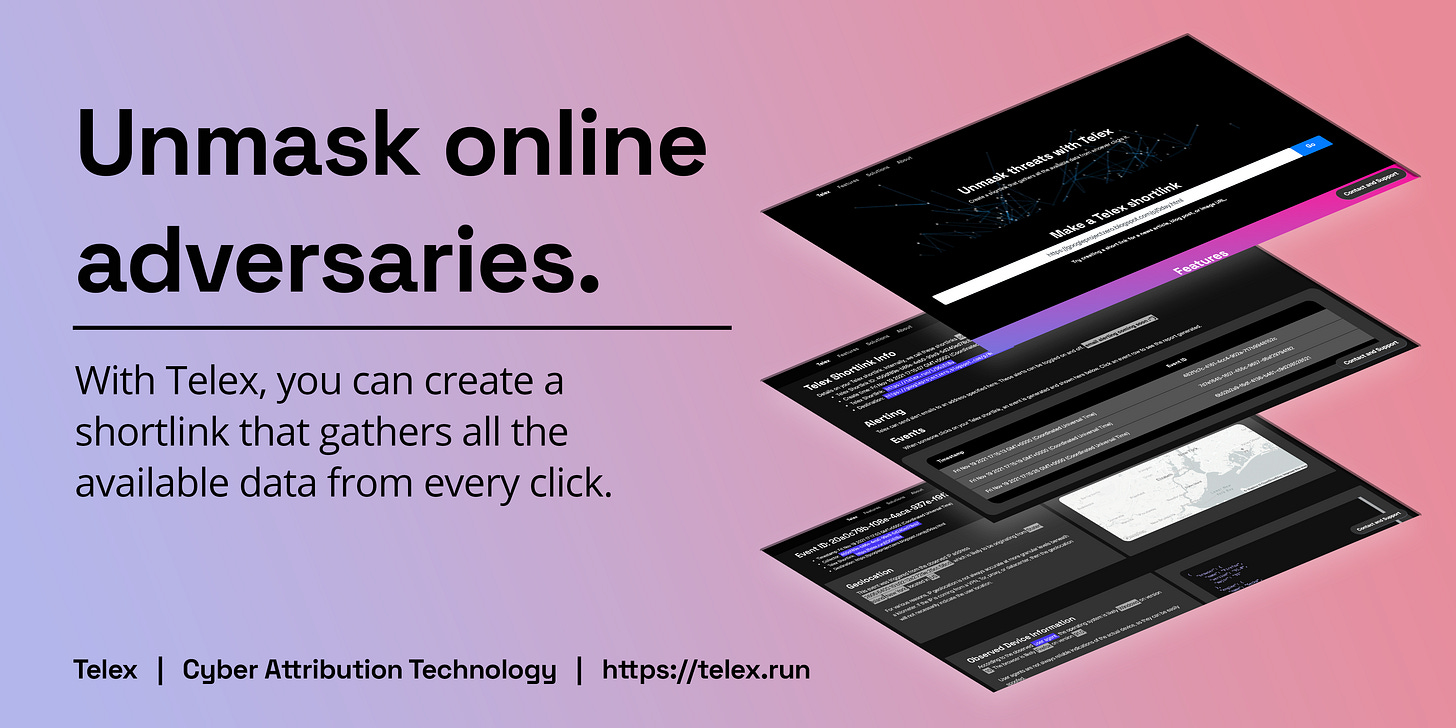
Unmasking online threats with Telex
Telex is a new, free tool designed to collect adversary intelligence against online threats.
Telex is a new, free tool designed to collect adversary intelligence against online threats. In this post, security researcher Aaron DeVera introduces Telex and demonstrates how it supports online investigations.
The web is an increasingly complex and scary place 1. People are increasingly aware of the threats and risks to their data, whether that threat is posed by cybercriminals 2 or large tech companies 3.
The information security industry is directly incentivized towards making products that protect corporations and the people who work for them. The wealth of security knowledge accumulated over decades by high-budget and high-cost security companies is gated 4 behind pricey EDR products and Threat Intel Platforms.
Everyday people looking to protect themselves online are left with a consumer VPN service, where your options range from benign 5 to sketchy 6 to outright nefarious 7. Or maybe you even have consumer antivirus software, which feels as stale as my America Online CD-ROM 8.
Since the death of Grumpy Cat, I keep asking myself: Is the web a more joyful place from when I first logged on in the 90s?9 Is it safer? And are we even getting the proper visibility on the threats to our everyday internet experiences?
Telex is a tool for unmasking threats
Telex is designed to be a tool easy enough for everyday internet users to use for their personal safety. But ultimately, Telex can serve all sorts of purposes for researchers, security operators, investigators, survivors of online abuse, and legal teams. It is designed to expand the data footprint on a target, and can be combined with other data you may have to create a holistic profile on a particular threat actor.
You may already enjoy using CanaryTokens for some of these purposes. CanaryTokens are shortened links that collect a little bit of info from whoever clicks on the link, before redirecting to the intended destination 10. Telex is like a canary on steroids! Like honeypots, it is are a great mechanism for capturing data about adversaries known and unknown.
Since it was created, Telex has already found a role in the hands of responsible operators:
Identifying cyberstalkers who are violating the restraining orders meant to protect abuse survivors
Collecting signals intelligence on those spreading disinformation on social media
Identifying the location of fraudsters sending text messages
Getting home network attribution on global malware developers
Attributing harassment campaigns to a particular network range
I look forward to seeing new uses of Telex as it reaches a broader audience in the security research and open source intelligence communities.
How to use Telex
Making a link with Telex is as easy as making a shortlink with a service like bit.ly or goo.gl.
First, paste a URL where you want a target to be redirected after clicking your Telex link.
Next, Telex will generate a control panel based on your link. On this page you will find your Telex shortlink. This is the link you will want to send to a target.
As people click on your link, events will appear in your control panel page. Telex will generate a detailed event report for each event as they’re detected. Here you’ll find various datapoints derived from the network session created by the target.
When sending a Telex shortlink to a target, you’ll see that the link preview matches the expected destination. This is crucial when working in the midst of threat actors, as security researchers often do.
Telex runs on Cloudflare Workers, and benefits from additional enrichment from Greynoise and IPInfo. We love these technologies and look forward to providing the full benefits of their telemetry to Telex users. Ultimately, the amount of data we collect is no more intrusive than that of a Google Analytics or Facebook Pixel. Telex is also not designed to store any of this data in a way that could be used for us to package and sell in bulk to a data broker. And in future releases, Telex users will have the option to select data retention policies that match their preference, including burn-after-use and 30/60/90-day retention periods.
Free to use, no sign-up required
Telex is now available today, as a free-to-use tool for anyone to add to their personal security toolbox. In the coming days, we will post some more details on how Telex works, and some early success stories in using it to catch cybercriminals.
As Telex moves out of Beta, you will find more features will be added, such as webhook-based alerting and options to customize what data is collected based on business need. And in the future, premium tiers of Telex will be offered extended capabilities for advanced use cases.
Happy hunting!
“Everything is overcomplicated,” Samuel Arbesman laments in this June 2021 piece for The Atlantic. The anecdote stems from the fact that an outage from an internet services provider caused downstream effects to major websites and services. Even just typing the above sentence is a broad generalization, as the “internet services provider” was Fastly, which is actually a content distribution network, which purely provides rapid edge services for other internet services. Case in point, everyday people know less and less about how the internet is being developed.
Have I Been Pwned projects more than 11.5 billion accounts have suffered a password breach.
Previous research estimated Facebook made about $140 from every North American monthly active user.
Gartner reports about a 7% increase in the size of the cloud services industry from 2019 to 2020, surpassing a $250 billion capitalization. The same report expects the downstream information security market to increase at a faster rate above 8% through 2024.
While they remain the most popular consumer VPN, NordVPN users often take to Reddit to complain about the company’s “shady” marketing tactics.
Look no further than the acquisition of PIA VPN to understand how consumer VPNs are ultimately incentivized to monetize user data.
Hackers are known to use several VPN providers due to their nihilistic stance on end user protection.
Guilty truth: In my earliest days on the web I was under the impression these CDs were required for internet connectivity.
A huge shoutout to Haroon Meer, whose thought leadership in the space I have long appreciated.





![[video-to-gif output image] [video-to-gif output image]](https://substackcdn.com/image/fetch/$s_!hDqd!,w_1456,c_limit,f_auto,q_auto:good,fl_lossy/https%3A%2F%2Fbucketeer-e05bbc84-baa3-437e-9518-adb32be77984.s3.amazonaws.com%2Fpublic%2Fimages%2F1e1cb1cd-502a-4748-806d-f184ac789e16_600x332.gif)
![[video-to-gif output image] [video-to-gif output image]](https://substackcdn.com/image/fetch/$s_!_78y!,w_1456,c_limit,f_auto,q_auto:good,fl_lossy/https%3A%2F%2Fbucketeer-e05bbc84-baa3-437e-9518-adb32be77984.s3.amazonaws.com%2Fpublic%2Fimages%2F0dcc4c9c-ab78-4121-9dca-4898a61ec5be_600x408.gif)
![[video-to-gif output image] [video-to-gif output image]](https://substackcdn.com/image/fetch/$s_!n7pA!,w_1456,c_limit,f_auto,q_auto:good,fl_lossy/https%3A%2F%2Fbucketeer-e05bbc84-baa3-437e-9518-adb32be77984.s3.amazonaws.com%2Fpublic%2Fimages%2Fa0764a84-cb66-4c85-816a-a08506f17e57_600x405.gif)
![[video-to-gif output image] [video-to-gif output image]](https://substackcdn.com/image/fetch/$s_!61rH!,w_1456,c_limit,f_auto,q_auto:good,fl_lossy/https%3A%2F%2Fbucketeer-e05bbc84-baa3-437e-9518-adb32be77984.s3.amazonaws.com%2Fpublic%2Fimages%2Fb818da57-5274-4e06-a23d-348fbe21272a_600x388.gif)