AgainstTheWest, the hacking group wreaking havoc on Chinese government and corporate targets
No targets in the Chinese Communist Party seem safe from this Western-aligned hacktivist.
Backchannel’s "Notes from the Underground” series aims to provide a spotlight on the cybercriminal underground by featuring interesting artifacts curated from threat actors. Content in this post may reflect the words and intentions of the threat actor, not Backchannel.
For archival sake, and lack of exogenous sources, this post will provide links to RaidForums posts. It is not recommended that you visit unless you are familiar with the terrain.
Since October 2021, a user going by “AgainstTheWest” (ATW) has published various data breaches and evidence of website defacements on the underground forum RaidForums. While RaidForums is not particularly known for housing high-tier, persistent threat actors, ATW has proven to be engaged in a weeks-long campaign against the People’s Republic of China, through cyberattacks targeting government and corporate entities tied to the Chinese Communist Party.
In this post, we’ll walk through a loose profile of ATW, looking into their motivations and characteristics, and then provide a timeline of ATW’s operations.

An estimated timeline of operations is provided in our analysis notebook linked here.
Long time listener, first time caller
ATW first appeared in on October 14, in a post to RaidForum’s Leaks Market section where they claimed to be putting up for sale hacked materials stolen from the Chinese central bank:
“we have been working for at least two months on this operation. It has allowed us to gain access to the People's Bank Of China internal assets.”
Like their profile picture of Max Headroom might suggest, there is sarcasm and trolling in ATW’s persona. “This is a virus. Reported,” they reply to someone’s idea of good music1. Ultimately, the impression given is that ATW knows how to use the forum; they know how sales work, they know the moderators and can intimate some knowledge of the forum’s history, and they talk like the locals. It is not likely that the October 14 account creation date was the user’s first visit to the site.
“Today I managed to deadlift 150kg / 330lb at my local gym. Pretty happy with myself :-)” ATW posts in a thread they created to discuss weightlifting, mere hours after disclosing alleged breaches of Alipay, a Chinese defense contractor, and civilian PII2. It’s almost as if ATW is right at home.
Not motivated by money
Though some of ATW’s earlier posts were put up for sale, many since then have been given away for free. “If this never sells, we'll probably just end up putting it up for free. Not really bothered by money,” they say in a reply to a thread of their breached Alibaba Cloud data3. This point is perhaps further demonstrated by their acceptance of Bitcoin and Ethereum, which can be trivially tracked, rather than the underground’s preferred currency, Monero. Ultimately, RaidForums does not usually have the reputation for a location where big deals for data or warez go down, as there are more serious and reliable forums for that.
“It would seem that we've pissed off China, finally”
Despite dabbling in targets that follow some sort of topical agenda4, for ATW it’s really all about China. Usually pointing to the Uighur genocide or aggression towards Taiwan, ATW claims that their motivations are in direct response to some sort of action conducted by the Chinese government.
We've noticed that China still refuses to back down from intimidating Taiwan. We'll continue to leak their shit until they stop.
It’s not clear that this feedback loop has yet to work in ATW’s favor. In fact, if media attention is one of the goals of ATW’s operations, they seem to publicly lament the lack of it: “Most of my shit still isn't being reported on,” they say in a Discord channel. “Guess China is really that spooky.”
So far the biggest piece in the public sphere on ATW is from Chinese cybersecurity firm Sangfor who took to the media site Sohu to write a technical report ATW’s breach of the People’s Bank of China5. In the analysis, Sangfor describes how Sonarqube servers were accessed due to older versions of the software allowing public access by default. This particular technique targeting this software fits the profile of some recent hacktivist activity; the FBI published a flash notification due to hacktivists targeting this software just last year6.
“It would seem that we've pissed off China, finally,” ATW comments in response to the Sangfor piece, criticizing it for several inaccuracies that were published.
AgainstTheWest’s Posting Behavior
In an analysis of about 300 ATW posts, we can attempt to understand the sort of “working schedule” that ATW has by basing all activity on the same 24-hour axis.
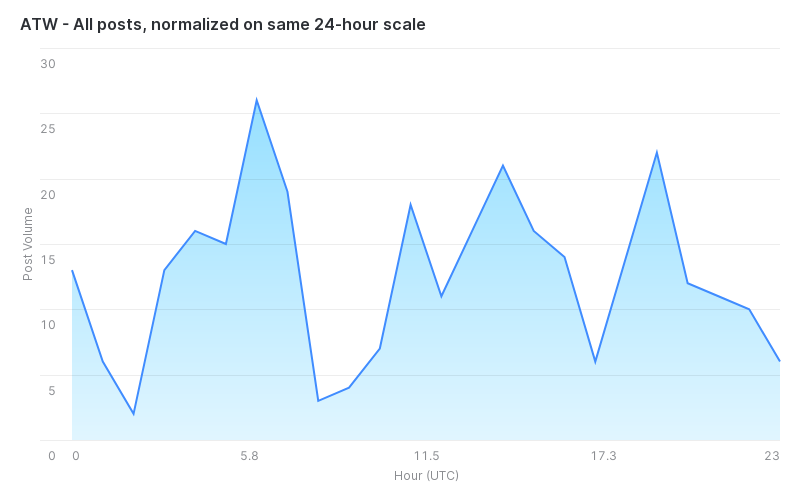
When removing thread creation from this dataset, you strictly get the volume of replies that ATW has made. This is useful in the scenario where ATW might be scheduling or automating thread creation.
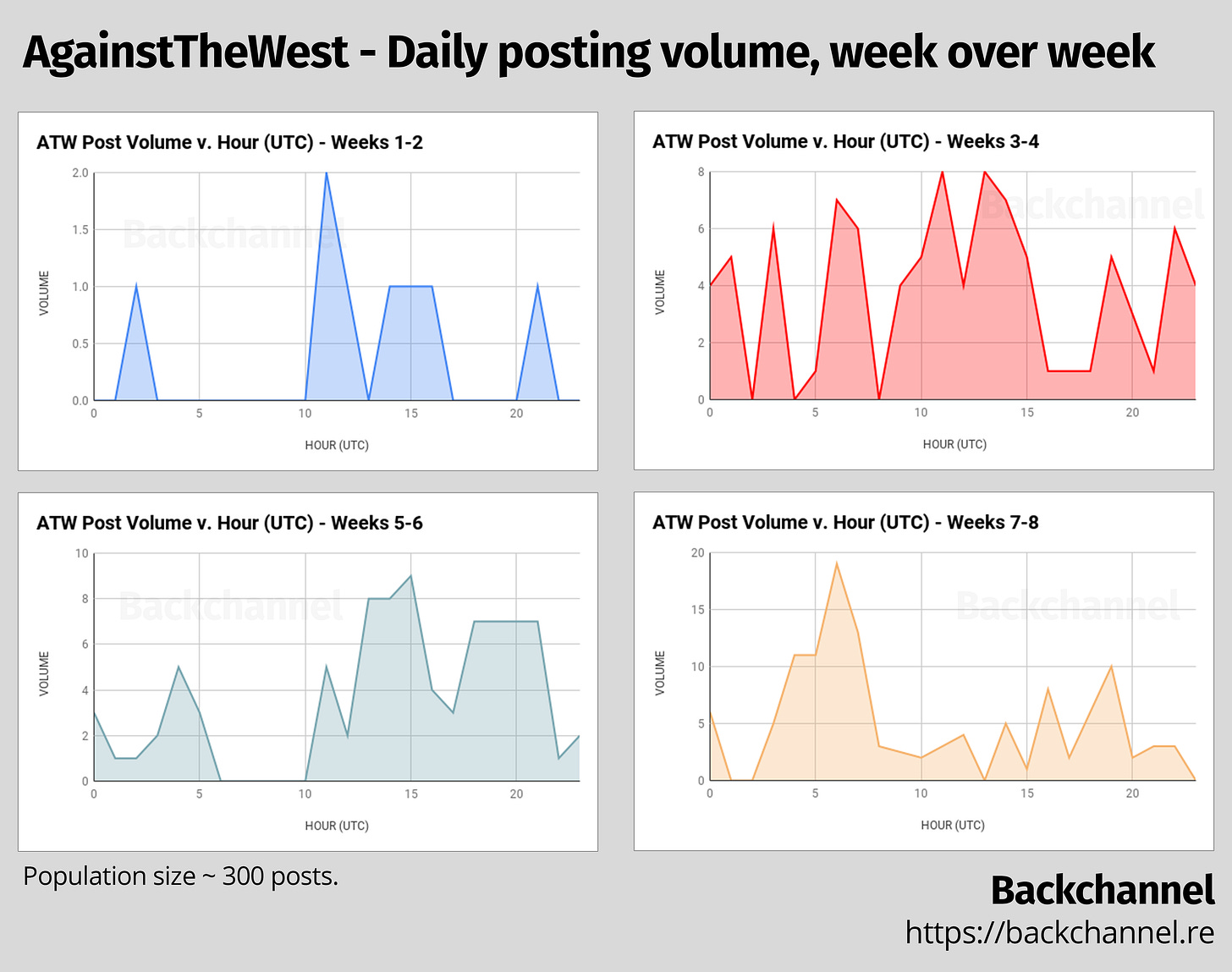
However, this may not be telling us the full picture. What if ATW’s schedule changed, either as a result of changing timezones, multiple operators, or an intentional decision to conform to a different schedule? One way to determine that is to extrapolate the 24-hour activity chart for each week of ATW’s operation on the forum.
A word bubble generated off of the posts to the forum may shed a little light on the language diversity used by ATW. It is not surprising that much of the language centers around the stated mission of ATW.

When removing the highly concentrated language, we may gain some additional insight into ATW’s writing patterns.

Authenticity and final thoughts
The straightforward nature of AgainstTheWest’s mission and operations perhaps lend credibility to the idea that they are who they say they are: an everyday RaidForums user with some nominal hacking skills and an ideological opposition to the Chinese Communist Party’s activities. Cybersecurity professionals may be quick to consider that some degree of deception is at play when a group who emerges from thin air, with varying degrees of credibility and the claimed mission of “hacktvism.” Many high-profile cases where hacktivism is referenced often end up being a cover for nation-state actors executing information operations 7 8.
But with AgainstTheWest, there is maybe a hint of authenticity. Between the lack of sophistication in their attack chain, or their transparent comfortability with RaidForums, ATW has some dimensions not consistent with the nation-targeting operations we know of. “It’s interesting because we in the United States often never hear this side of it,” says Juan Andres Guerrero-Saade9, a Principal Security Researcher at SentinelOne. “You typically hear of cyberoperations targeting us.” In November, Guerrero-Saade gave a talk at CyberWarCon about the use of hacktivism as a cover for nation-state information operations 10. One trend between the operations featured in the talk were that they usually had a single objective, little work going beyond that scope. “One thing about this profile is that they’re leaned into the hacktivist aesthetic, coming up with targets as they go,” says Guerrero-Saade. “Keeping up with that persona would take work.”
The unique profile of AgainstTheWest makes it worth keeping up with, where we may learn more about their motivations or background. We will continue to watch AgainstTheWest as they continue their operations.
An estimated timeline of operations is provided in our analysis notebook linked here.
https://raidforums.com/Thread-OJ-X-TR-Back2Back?pid=4611207#pid4611207
https://csrc.nist.gov/glossary/term/PII
https://raidforums.com/Thread-SELLING-Chinese-Alibaba-Cloud-Aliyun-ALL-PLATFORM-SRCs-Frontend-Backend-2021-ATW?pid=4603507#pid4603507
Threads with alleged breaches from Poland and Russia both followed newsdays where either country was in the news for some sort of hawkish activity.
https://www.sohu.com/a/502400487_244641?_x_tr_sch=http&_x_tr_sl=zh-CN&_x_tr_tl=en&_x_tr_hl=en&_x_tr_pto=nui,sc
https://www.documentcloud.org/documents/20399900-fbi_flash_sonarqube_access_bc
Perhaps most famous is Gufficer 2.0, a persona maintained by Russian Intelligence Services. https://en.wikipedia.org/wiki/Guccifer_2.0
Far more comedic (and my personal favorite) is the Guardians of Peace. https://en.wikipedia.org/wiki/Sony_Pictures_hack
https://twitter.com/juanandres_gs
https://www.cyberwarcon.com/last-cover-for-action





