Notes from the Underground: LockBit ransomware group pays out first known bug bounty
The notorious LockBit ransomware group announces their first public bug bounty payout, and claims insider sources within cybersecurity company.
Backchannel’s "Notes from the Underground” series aims to provide a spotlight on the cybercriminal underground by featuring interesting artifacts curated from threat actors. Content in this post may reflect the words and intentions of the threat actor, not Backchannel.
The content in this post is sourced from the LockBit ransomware group themselves, and cannot be independently verified at this time.
Highlights
On or around 2022-09-17, LockBit ransomware group announced on their blog that they paid out a bug bounty to a security researcher who contacted them. It is the first payout LockBit has publicly acknowledged since they first announced the bug bounty program in June 2022.
In the post, LockBit also claimed to have received insider information from the US law enforcement and Coverware, a cybersecurity company specializing in ransomware recovery. LockBit claims to have received tips regarding their “competitors' encryption systems”.
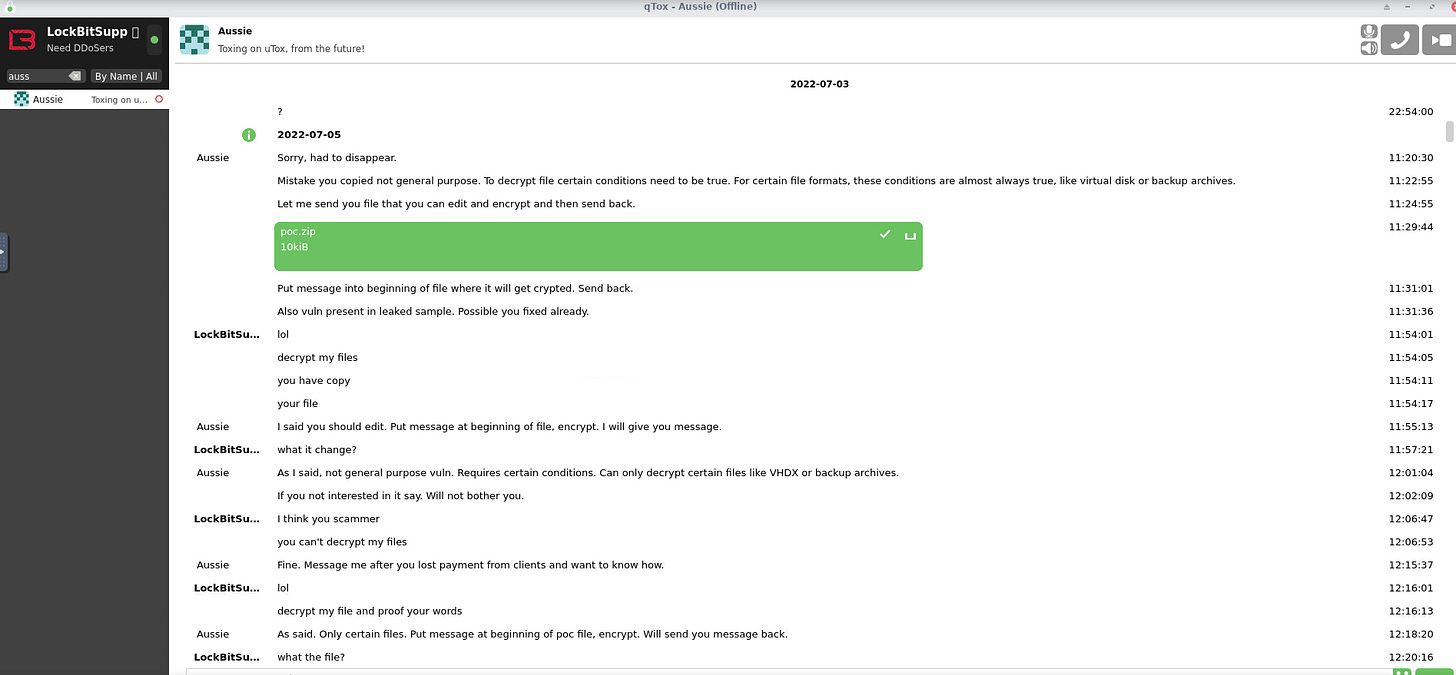
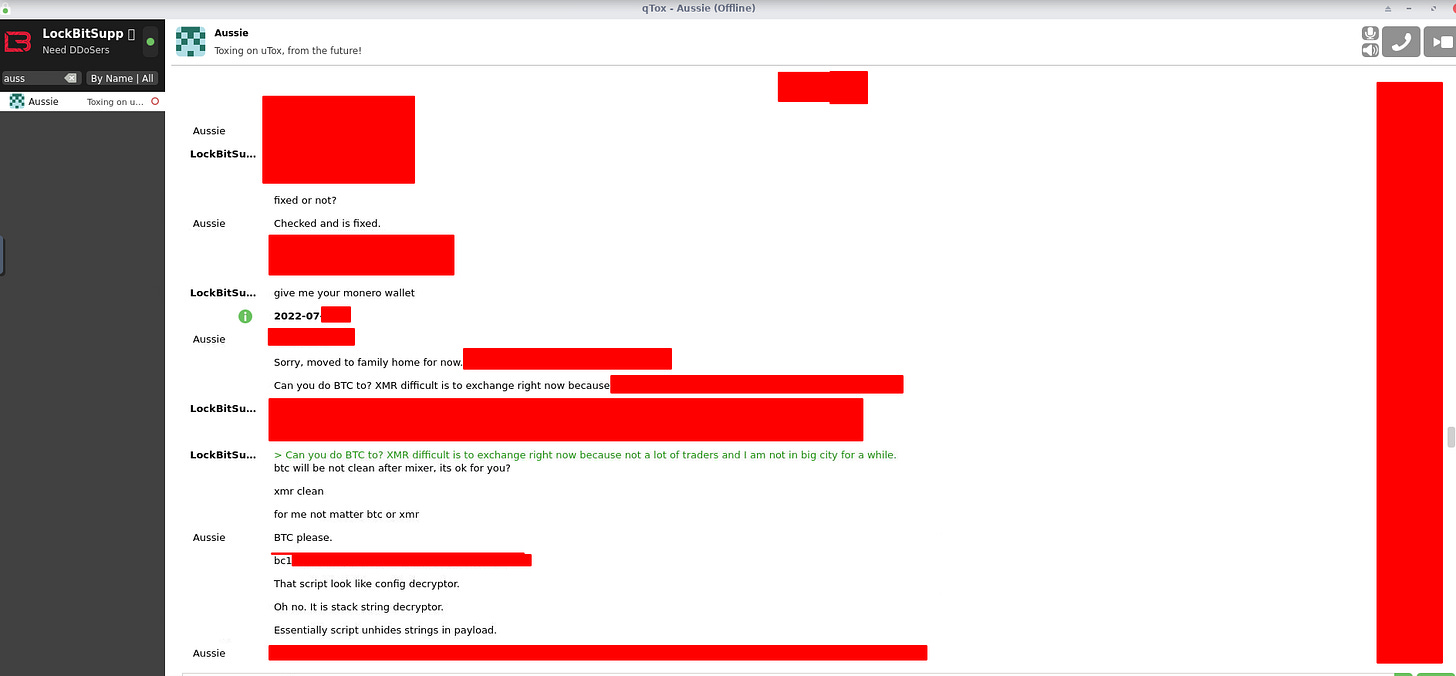
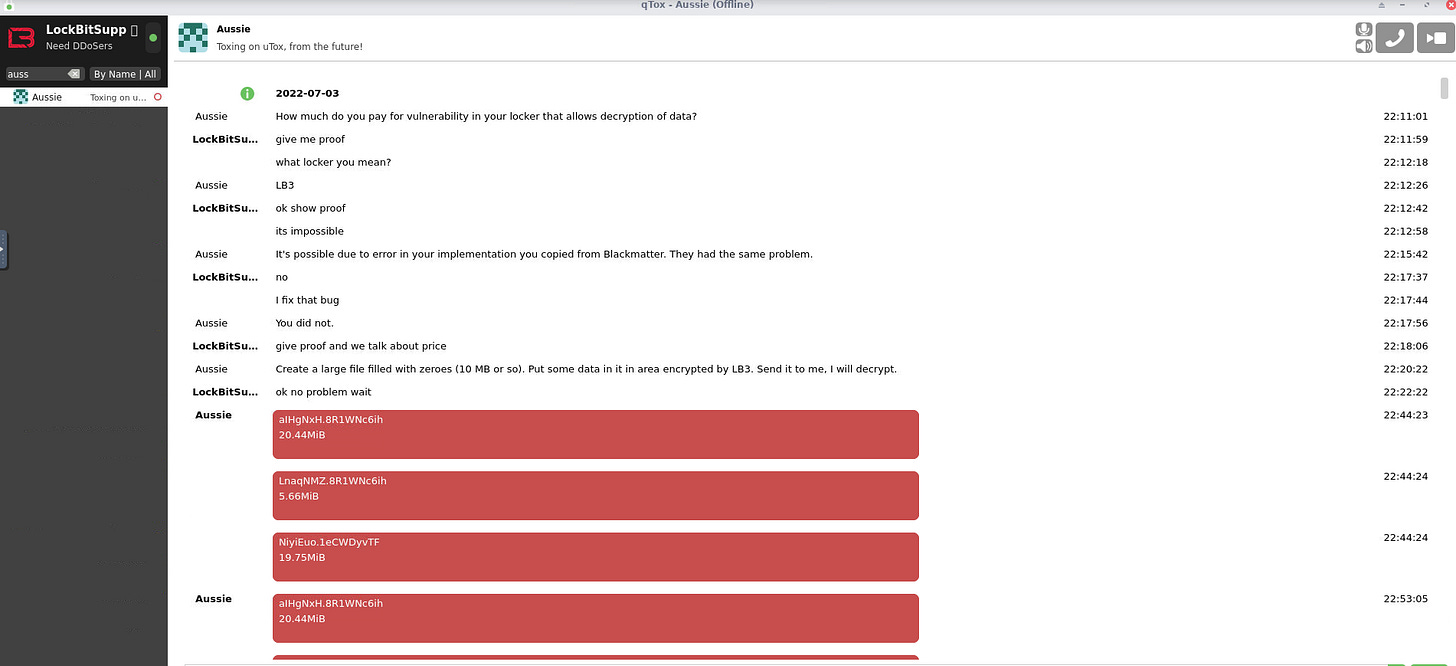
Attached to the post are communications between LockBit and the security researcher who allegedly found a vulnerability in the LockBit crypter. The conversations are over Tox messenger.
Original Post Contents
Title: “First bounty payout $50,000”
Uploaded: 17 Sep, 2022 02:39 UTC
Updated: 17 Sep, 2022 02:39 UTC
Post below:
On July 6, 2022, the first bounty payment of 50 thousand dollars was made for the bug report in the encryption software, which was fixed on the same day. The bug was that it was possible to decrypt any vmdk or vhdx file for free, since the beginning of these files begins with zeros. In order to minimize the damage and the impact of payments for the decryptor from the current attacked companies, it was decided to postpone the public announcement of the award until the current day.
Also, thanks to the recommendations of the good man, encryption algorithm was changed in linux vmdk files encryptor, now each vmdk file is disclosed and the encryption of files inside is done, such functionality not a single affiliate program on the planet.
A very special thanks to the FBI agent and Coverware contributor who keeps me up to date with the latest information. Thanks to the insider information we have learned about the weaknesses and bugs in our competitors' encryption systems.
We are grateful for every message that will be helpful to us.
Also we are looking forward to more insiders and researchers, do not hesitate to write tox, we will find money for each of you.
Thank you for participating in our bounty program.
Images attached in the original LockBit post: